The Incident Response podcast
BDIR Podcast Episode-009 - MITRE ATT&CK Part 2
TOPIC: TORA TORA TORA - MITRE ATT&CK Part 2
SPONSORS OF OUR PODCAST
NEWS-WORTHY:
Data Breaches in the Last 30 Days Affect A Billion People - WAAY 31 ABC
Q&A website Quora was hacked this week as well, potentially exposing data and private messages from 100 million users.
The FBI is investigating a cyber breach of the National Republican Congressional Committee
Dell, the computer company, announced a security breach although it does not believe consumer data was exposed.
The city of Ames, Iowa had its parking ticket system breached, exposing ticket payer data.
Dunkin' (formerly Dunkin Donuts) had its perks reward club database hacked.
Atrium Health had 2.6 million patient records exposed
A breach potential exposed Medical Informatics Engineering’s 3.9 million patient records across 12 states.
41,000+ cancer patients had their records potentially exposed at Cancer Center Treatment of America's Arizona facility.
Vision Direct handles payments for Visa, Mastercard, Maestro, and PayPal. It got hit.
Millions of passengers of Cathay Pacific airline are at risk from a security breach.
Also breached: US Postal Service, 1-800-Flowers, Butler County, OH's HIPAA records, and Nordstorm.
Did we mention breaches at: Amazon, 1-877-Kars-4-Kids, Florida Department of Health, or Healthcare.Gov, or Commonwealth Bank?
Dell Forces Password Reset for Online Customers Following Data Breach
Marriott Starwood breached - Sheraton users beware...
https://krebsonsecurity.com/2018/11/marriott-data-on-500-million-guests-stolen-in-4-year-breach/
Kroll offers monitoring of your breached information on the Dark Web for FREE to affected users
SITE-WORTHY
1. Malware Archaeology - Home of the ‘WIndows Logging Cheat Sheet(s)‘
2. MITRE ATT&CK website
TOOL-WORTHY
KANSA - PowerShell IR tool
2. KANSA-LOG-MD - Coming SOON
MALWARE OF THE MONTH
LOKIBot
Delivered by Word Doc, EXE, or MSI from a link or attachment in and email
MSI
MSI Installer user interaction with GUI, so user has to approve installation
The user sees the installer start if you agree, of course people do
After it installs it just disappears
Places the payload in C:\Windows installer, an MSI feature
Deletes from Windows Installer and then places itself in C:\Users\<Bob>\AppData\Roaming with a name of Androidsomething in this sample
Directory is attrib +S +H as is the file
The original MSXYZ.tmp is loaded in memory, the copy on disk is not loaded
Did not seem to have a persistence, maybe time delayed longer than we saw
It was easily visible in Running Processes, a new feature of LOG-MD-Pro
The .tmp file also called out to a C2 server
Lesson Learned
BLOCK MSI attachments, no reason this should come in from email
If received from a link, that is more of a challenge
Check your running processes for items that are no longer on disk, so cannot be hashed, always bad
Look for parentless processes as MsiExec was the parent of the .tmp file that was loaded.
Same hash as the .EXE stored under \Roaming
TOPIC OF THE DAY
Mitre ATT&CK - TORA TORA TORA - PART 2
Listen to Part 1 with Katie Nickels from MITRE and the Show Notes here:
Articles:
At the end of the Show Notes
MITRE ATT&CK
MITRE ATT&CK Evaluations
The Malware Management Framework
Why is ATT&CK useful?
How do we go about using it?
Where do we start?
Let’s talk about Cheat Sheets…
What do the Cheat Sheets and ATT&CK have in common?
Windows ATT&CK Logging Cheat Sheet
Windows ATT&CK LOG-MD Cheat Sheet
ARTICLES:
MITRE ATT&CK
Please contribute to ATT&CK! Email us at attack@mitre.org
Watch the ATT&CK Con 2018 YouTube videos
https://youtu.be/NVgqx7M1K20 - Day 1 morning
https://youtu.be/_HSkva44lFo - Day 1 afternoon
https://youtu.be/LxzVtfw4WyQ - Day 2 morning
SANS THIR (Threat Hunting & Incident Response Summit - New Orleans 2018
https://www.sans.org/event/threat-hunting-and-incident-response-summit-2018/summit-agenda
Watch for the Presentations and Videos to be published
Marriott Starwood/Sheraton Breach
Free WebWatcher Enrollment
Marriott is providing guests the opportunity to enroll in WebWatcher free of charge for one year. WebWatcher monitors internet sites where personal information is shared and generates an alert to the consumer if evidence of the consumer’s personal information is found. Due to regulatory and other reasons, WebWatcher or similar products are not available in all countries. Guests from the United States who complete the WebWatcher enrollment process will also be provided fraud consultation services and reimbursement coverage for free.
The section below provides additional information on steps you can take. If you have questions about this notification and to enroll in WebWatcher (if it is available in your country), please visit info.starwoodhotels.com.
* Starwood brands include: W Hotels, St. Regis, Sheraton Hotels & Resorts, Westin Hotels & Resorts, Element Hotels, Aloft Hotels, The Luxury Collection, Tribute Portfolio, Le Méridien Hotels & Resorts, Four Points by Sheraton and Design Hotels. Starwood branded timeshare properties are also included.RDP Thriving on the Dark Web
Endgame - Putting the MITRE ATT&CK Evaluation into Context
Dark Reading - MITRE Changes the Game in Security Product Testing
JPCert Detecting Laternal Movement
-----------------------------------------------------------------------------------------------
BDIR Podcast Episode-008
TOPIC: EPIC FAILURE, Who Do You Blame? You decide
SPONSORS OF OUR PODCAST
NEWS-WORTHY:
A tweet from Dave Kennedy on TrustedSec efforts
“On a screenshare with my team on an engagement watching our completely custom exploitation framework + C2 being deployed and using undoc techniques all the way through with a ton of EPP/EDR products on the endpoint without detection. Proud of the research team and #TrustedSec :)“
NSS Labs fires off anti-malware-testing lawsuit at infosec toolmakers
Are they colluding to NOT fail the tests?
The report "Endpoint Detection and Response Market by Component (Solution and Service), Enforcement Point (Workstations, Mobile Devices, Servers, POS Terminals), Deployment Mode, Organization Size, Vertical, and Region - Global Forecast to 2021", The EDR market size is estimated to grow from USD 749.0 million in 2016 to USD 2,285.4 Million by 2021, at an estimated Compound Annual Growth Rate (CAGR) of 25.0%.
Download the full report: https://www.reportbuyer.com/product/5485541
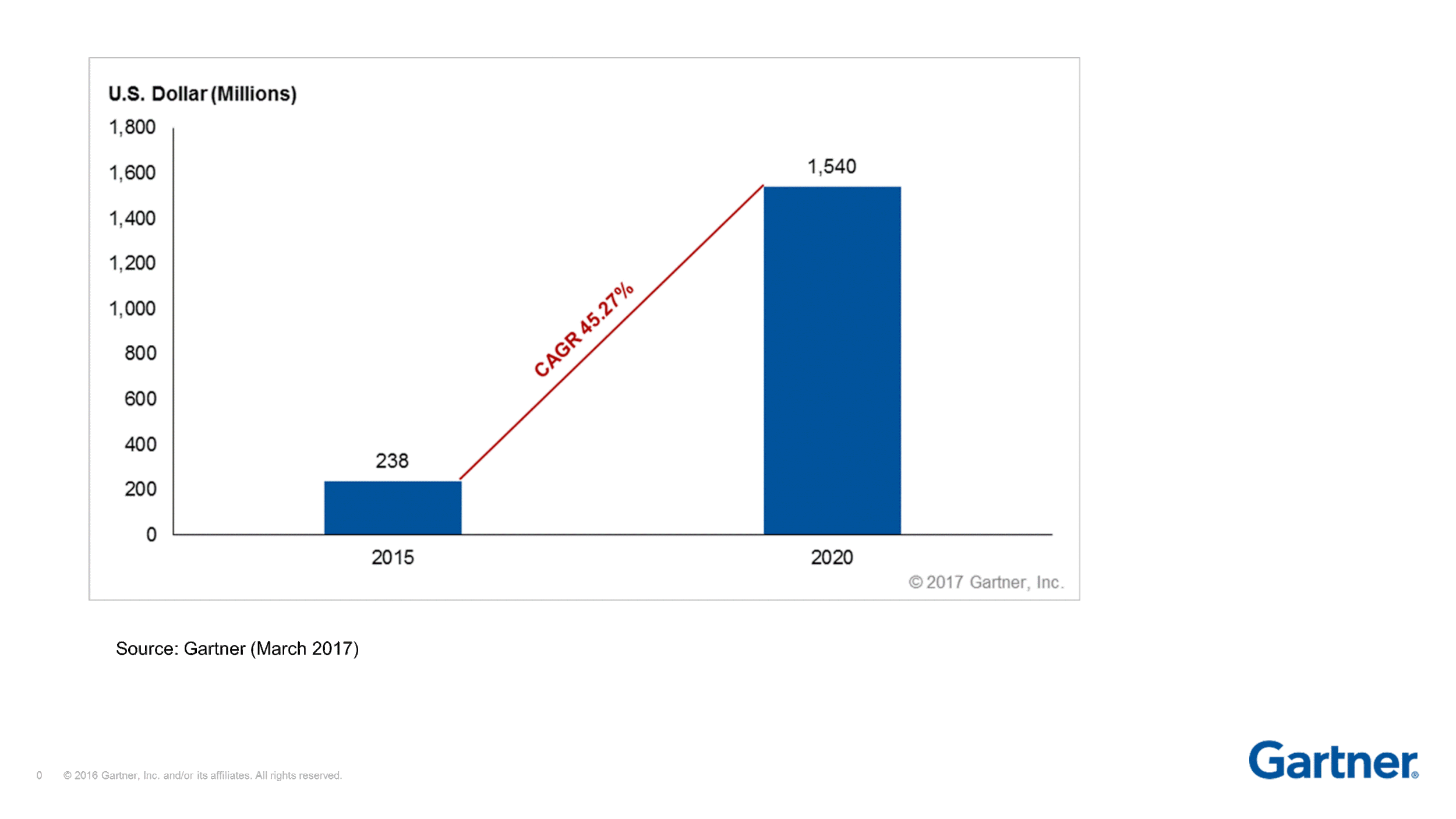
Gartner says EDR will be a 1.5 BILLION, with a B business by 2020
Michael’s DerbyCon 2017 talk on Testing EDR
Michael and BRIAN talk Credential Stealing at BSides Austin 2018
Forrester Report on is EDR overblown
Interesting quote from the article
“At its core, EDR turns your infrastructure into a fabric of queryable systems with scalable remote management capabilities and the ability to detect abuse. Done. That’s it. This is only tangentially a security tool and it’s time to reframe how we think about EDR into that of a SecOps tool”
SITE-WORTHY
1. None this episode
TOOL-WORTHY
None this episode
MALWARE OF THE MONTH
None this episode
TOPIC OF THE DAY
EPIC FAILURE, Who Do You Blame? You decide
ENVIRONMENT
Less than a dozen offices
Network devices with IPS
DNS Proxy on all endpoints
MSP Agent
EDR agent
No Admin rights on endpoints
DevOps app deployed nightly
POINT OF ENTRY
With all this in place, A brute force against an Internet facing RDP server open for employee use and subsequent infection of over 150 assets within 20 minutes of initial infection (Patient 0).
RECOVERY
The Volume Shadow Service (VSS) retention period was at the default retention period is too short such that by the time the root cause was found and went to roll back infections, VSS had already written infected files to storage and rollback wasn't an option.
INVESTIGATION
The first infection Credentials were circumvented due to the threat agent using the System Management software suite (name a few) to kill the EDR services then infect the machine.
The EDR vendor did everything they could to understand and report on the issue. They paid to have the server shipped to them where they completed a full forensic analysis subsequently proving how the service was terminated and then infected.
The 2nd infection, was missed by EDR but was caught by AV that was installed the same day to see what it would find.
They do know the current recommendation from IT Security thought leaders is to use a blended solution like EDR and AV. But money isn't endless for clients so that may be problematic.
A Log Mgmt solution was deployed after the fact and discovered a lot happening in the environment of which stunned the staff.
EDR Vendor position
The position was taken the open RDP connection was the root cause and EDR was not at fault for not catching or rolling back the infection.
So let’s look at what they did RIGHT…
Endpoint users were not admins
EDR on the endpoints
DNS proxy agent on the endpoints
DevOps pushed out updates nightly
So let’s look at what went wrong here...
RDP Facing the Internet
RDP on the Internet with just username and password is one, if not the RISKIEST things you can do as a company, goes for all Remote Access
If you don’t use 2-Factor AND collecting login attempts, you WILL get owned
The credential that was brute forced turned out to be an admin account with access to their System Management Software solution
They did NOT look for, or detect the brute force of an Internet facing system for remote access
The account used for System Management Software had access to the Internet?
Accounts for remote access should not have admin access, use a separate account that has to be entered once logged in to reduce this type of threat, consider a jump host to get to these management solutions
Logging was not enabled or used until after the event started
Logs were not collected or managed in any way
Logging was used only AFTER the event started, where they saw a stunning amount of information
No AV, just EDR was installed
EDR was stopped by an approved System Management solution designed to do this type of activity
The System Management solution was not being monitored for access
The EDR vendor did not seem to have a service status option (a flaw with many Security tools, if the agent is stopped, how is it detected? The Windows Advanced Logging Cheat Sheet” covers this type of non-Windows service permission changes to capture logging of services that are stopped
ARTICLES:
FireEye Baselining RDP
RDP Thriving on the Dark Web
Using RDP? Make your business less of a target for Ransomware
Gartner’s 2018 Magic Quadrant for Endpoint Protection Platforms (EPP): What’s Changed?
Endpoint Detection and Response: A New Wave in Security?
-----------------------------------------------------------------------------------------------
BDIR Podcast Episode-007
TOPIC: A little known guide of hacking tactics - ATT&CK - PART 1 (TORA TORA TORA)
OUR GUEST WILL BE:
Katie Nickels, ATT&CK Threat Intelligence Lead, MITRE
@likethecoins and @MITREattack
SPONSORS OF OUR PODCAST
NEWS-WORTHY:
Credit Freezes after Sept 21st, 2018 are FREEEEEE
Brian Krebs article
Track your luggage or Tracking YOU ?
"Do you use a Tumi bag? Registered it with Tumi's Tracer service? Your bag might not be the only thing being tracked. A reliable source we know told us that one way or another, Tumi may have lost track of the details of users who registered their bags with the service, and that whoever got a hold of it could use it for sophisticated phishing campaigns."
British airways website hacked 380K users affected
Tesla Model S and X cars can be REMOTELY opened
TOR Browser 0-Day
Bad Actors Sizing Up Systems Via Lightweight Recon Malware
https://threatpost.com/bad-actors-sizing-up-systems-via-lightweight-recon-malware/137364/
List of Admin and Application Whitelisting commands you should monitor the quantity of executions:
SITE-WORTHY
1. BDIR - Olaf Hartong Sysmon Modular
2. BDIR - Roberto Rodriguez @Cyb3rWard0 - Threat Hunter Playbook
Guest - Katie Nickels
MITRE ATT&CK website
TOOL-WORTHY
BDIR - Sysmon View and Sysmon Shell
Guest - Katie Nickels
MITRE ATT&CK Navigator
MALWARE OF THE MONTH
EMOTET - 2 Samples
Sample 1 - Word Doc
PowerShell BASE64 blob to hide download
Use of DOS Cmd line obfuscation
Extracted to AppData\Local\Microsoft\Windows\slskey.exe (root of folder)
Another long random.exe renamed same hash
Also \Users\Public 203.exe - root of folder (never good)
Lots of .tmp files in users tempt made by slskey.exe
Typical Run Key persistence
Changed Firewall Policy for Remote Assistance (Different Log !!!)
WerFault, so something crashed, watch those logs too
Sample 2 - EXE
Deleted loader/installer upon execution
Typical Run key persistence
AppData\Local\Microsoft\Windows\random_chars.exe
2nd copy, different hash in ProgramData root (Duh)
3rd copy in ProgramData\GUID folder different hash
Created a scheduled task name of a GUID
Folder and Task name GUID’s did not match
Lesson Learned
Because we are so quick at LOG-MD evals, the malware could wait to do more
In one sample it created a task 5 mins or more after running LMD. The Run Key was caught, but another version stored in ProgramData made a Scheduled Task
Remember what we said on the last podcast… ENABLE Scheduled Task logging !!!
Launch Chrome BEFORE malware eval.. Damn Google Update schedule tasks
You might Audit C:\Windows\System32\Tasks folder for Adds
TOPIC OF THE DAY
A little known guide of hacking tactics - ATT&CK - PART 1 (TORA TORA TORA)
INTERVIEW WITH: Katie Nickels of MITRE ATT&CK
So what is ATT&CK all about?
What is ATT&CK?
What is the goal of the project?
Why should people care about this project?
What are the components of ATT&CK
What are you working on that is coming up?
ARTICLES:
MITRE ATT&CK 101
The Design and philosophy of ATT&CK
Cyber Analytics Repository:
CAR Exploration Tool (CARET):
Katie’s blogs on applying ATT&CK to threat intelligence: Part 1 and Part 2
Katie and her colleague John Wunder’s BSidesLV slides (YouTube video coming soon!)
Upcoming events for Katie and the team:
Katie is briefing at the FireEye Cyber Defense Summit on October 3-4
Catch a few team members attending Derbycon
ATT&CKcon is on October 23-24 (it will be live streamed if you can’t make it in person)
Follow us on Twitter @MITREattack for updates
Contribute !!!
Please contribute to ATT&CK! Email us at attack@mitre.org.
-----------------------------------------------------------------------------------------------
PART 2 - A little known guide of hacking tactics - ATT&CK - PART 2
We will discuss some new Cheat Sheets and what to do with them and why we created them, and some other info you can use
BDIR Podcast Episode-006
TOPIC: Logging - How many tricks does it take to get to the center of a Log-iPop?
OUR GUEST WILL BE:
Jim Schwar, Lead Analyst (Cybersecurity)
Twitter - @jimiDFIR
SPONSORS OF OUR PODCAST
NEWS-WORTHY:
The most expensive Cyber attack EVER !!! (wired)
Not-Petya is estimated to have cost 40 BILLION US Dollars.
City of Atlanta 17 million Ransom Event
More on the costs of the City of Atlanta Ransomware attack, cost 17 MILLION US Dollars
APT32 proves what we say about logging - Monitor Scheduled Tasks
Why Malware Management, some might say Threat Intel is so important to consume and identify artifacts. Hunt for Scheduled Tasks in your environment
MALWARE OF THE MONTH
Sadly, none of interest this month ;-(
SITE-WORTHY
1. BDIR - Mitre ATT&CK
Guests - Jim Schwar
Harlan Carvey's Blog
TOOL-WORTHY
BDIR - WinLogBeat and FileBeat
Sample WinLogBeat and FileBeat .ymk files to start with
Guests - Jim Schwar
Splunk - Splunk.com
TOPIC OF THE DAY
Logging - How many tricks does it take to get to the center of a Log-iPop?
This all started with a Tweet: Jim tweeted - “SIEM is incredibly hard and complex to do right. It takes hundreds/thousands of man hours to tune it well and have rich actionable data. But most people want a quick fix, so they fail miserably”
Michael's response “Mmmm disagree” and this podcast was born
INTERVIEW: Jim Schwar
So what is difficult about audit logging?
Enabling it
Set the “right” things
Collecting it
Parsing it
The SEIM/Log Management solution
Queries
Alerts
Refinement
Endpoint collection ?
Reduction of noise
AV and Logging Agent
Specifically Events Codes:
4624 - Success login
4625 - Failed logon
4634 - Logged off
4647 - User initiated logoff
4648 - A logon was attempted using explicit credentials
What are you looking for ?
NOT winlogon, lsass or svchost?
Target different from the host?
4688 - Process Created
4768 - Kerberos Auth
4769 - Kerberos Service Ticket was requested
Kerberoasting detection
Fail_Code="0x0" | where Ticket_Enc_Type="0x17"
4770 - Kerberos Service Ticket was renewed
4771 - Kerberos Pre-Auth
Be the 1%
Jim Scwar - @jimiDFIR DMs open...
Brakeing Down Security Slack Channel - join to associate with the like minded
ARTICLES:
Malware Management
How to get started using IR Analyst reports to detect and hunt for artifacts
Extra Data in Windows Event Logs
This really only pertains to older systems, but it can save a lot of space if you are a high volume shop (I know cutting out the event descriptions has saved over 100 gigs a day)
The default linux kernel settings are not sufficient to high volumes of data (i.e. log servers), and tuning needs to be done for various items. But the biggest pain points for me are:
Read/Write Memory and Packet backlog
This document is for the Splunk Streamapp, but the same settings are relevant for any syslog server.
Transparent Huge Pages
https://dbakerber.wordpress.com/2015/03/11/update-on-hugepages-rewrite-to-fix-formatting-issues/
https://answers.splunk.com/answers/188875/how-do-i-disable-transparent-huge-pages-thp-and-co.html
ulimits
CONNTRACK
Keeps track of connections too long, and does not have enough entries for a host with a lot of systems connecting on ephemeral ports
Splunk UF depends on Windows Event Log Service
The basic problem here is, the UF will start to corrupt logs if it is started before the Event Log service, or if the Event Log service is restarted due to patching, etc… They way to resolve the issue is to make the service dependent on the Event Log service with a tweak the the UF’s service startup with a registry key.
This issue has existed since at least 6.3 and Splunk support refuses to add the registry key by default, make this widely known, or at the very least add a flag to the installer to add the keys. So you have to either push it through GPO or some other method in an environment.
It is also good to run a daily check of logs for the string "FormatMessage error" to find out which hosts are corrupting their logs and restart the service. An “empty” app on a deployment server that is set to restart the agent can be pushed out by Splunk Admins to resolve the problem if a support team or other management options are available.
Time Consuming Issues, that need to be dealt with consistently
Are the agents installed on all of your assets?
Is the data coming in clean?
Are there any broken systems that are generating tons of error logs? (A single host can jam up logging for hundreds/thousands)
Are appliances (specifically network devices) still configured to send the appropriate details of logs?
New hosts sending data that require a syslog filter to be updated. (This can largely be minimized by sending different types of hosts to different log ports)
Time formats in different log formats.
Message data NOT needed in your log to shrink the size of the message being consumed into Log Management
Reduce the misc, message data IN YOUR LOGS WHEN CONSUMING THEM. Blow tHIS AWAY.
4624
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
The authentication information fields provide detailed information about this specific logon request.
Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
Transited services indicate which intermediate services have participated in this logon request.
Package name indicates which sub-protocol was used among the NTLM protocols.
Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
4625
This event is generated when a logon request fails. It is generated on the computer where access was attempted.
The Subject fields indicate the account on the local system which requested the logon.
This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The Logon Type field indicates the kind of logon that was requested. The most common types are 2 (interactive) and 3 (network).
The Process Information fields indicate which account and process on the system requested the logon.
The Network Information fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested.
4634
This event is generated when a logon session is destroyed. It may be positively correlated with a logon event using the Logon ID value. Logon IDs are only unique between reboots on the same computer.
4647
This event is generated when a logoff is initiated but the token reference count is not zero and the logon session cannot be destroyed. No further user-initiated activity can occur. This event can be interpreted as a logoff event.
4648
This event is generated when a process attempts to log on an account by explicitly specifying that account’s credentials. This most commonly occurs in batch-type configurations such as scheduled tasks, or when using the RUNAS command.
4688
Token Elevation Type indicates the type of token that was assigned to the new process in accordance with User Account Control policy.
Type 1 is a full token with no privileges removed or groups disabled. A full token is only used if User Account Control is disabled or if the user is the built-in Administrator account or a service account.
Type 2 is an elevated token with no privileges removed or groups disabled. An elevated token is used when User Account Control is enabled and the user chooses to start the program using Run as administrator. An elevated token is also used when an application is configured to always require administrative privilege or to always require maximum privilege, and the user is a member of the Administrators group.
Type 3 is a limited token with administrative privileges removed and administrative groups disabled. The limited token is used when User Account Control is enabled, the application does not require administrative privilege, and the user does not choose to start the program using Run as administrator.
4768
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options, encryption types and result codes are defined in RFC 4120. EditMore Resources
4769
This event is generated every time access is requested to a resource such as a computer or a Windows service. The service name indicates the resource to which access was requested.
This event can be correlated with Windows logon events by comparing the Logon GUID fields in each event. The logon event occurs on the machine that was accessed, which is often a different machine than the domain controller which issued the service ticket.
Ticket options, encryption types, and failure codes are defined in RFC 4120.
4770
Ticket options and encryption types are defined in RFC 4120.
4771
Certificate information is only provided if a certificate was used for pre-authentication.
Pre-authentication types, ticket options and failure codes are defined in RFC 4120.
If the ticket was malformed or damaged during transit and could not be decrypted, then many fields in this event might not be present.
-----------------------------------------------------------------------------------------------
BDIR Podcast Episode-005
TOPIC: WMI - Exploitation and Detection
OUR GUEST WILL BE:
Chris Truncer - FortyNorthSec
Twitter - @ChrisTruncer and @FortyNorthSec
Blog - https://www.fortynorthsecurity.com/blog
Github - https://www.github.com/FortyNorthSecurity
SPONSORS OF OUR PODCAST
NEWS-WORTHY - Sysinternals release Sysmon 8.0 and AutoRuns 13.90
Mark and crew over at Microsoft have release updates to two popular tools in Sysmon and AutoRuns. Sysmon 8 adds a RuleTag field so now you can label your rules and see the rule name in the logs data. Autoruns fixed data involving WMI, the topic of the day.
Reminder - Do NOT upload files to VirusTotal until you are certain you are not going to disclose anything to the criminals as they will know, that you know about their Fu. Also, anything you upload can be downloaded by anyone with a VT Private Key and if you upload documents with confidential data, you may create a disclosure for yourself.
MALWARE OF THE MONTH
Sadly, none of interest this month ;-(
SITE-WORTHY
1. BDIR - WMI vs. WMI: Monitoring for Malicious Activity
2. Abusing WMI Providers for Persistence
Guests - Chris Truncer
Device Guard Bypass Mitigation Rules
https://github.com/mattifestation/DeviceGuardBypassMitigationRules
WMI Implant Blog - https://www.fortynorthsecurity.com/out-of-the-box-wmimplant-detection-opportunities/
Some IR Tools - https://github.com/Invoke-IR
Matt Graeber's Blog - http://www.exploit-monday.com
TOOL-WORTHY
BDIR - WMILM - Phillip Tsukerman
2. LOG-MD-Pro of course, new WMI persistence feature
Guests - Chris Truncer
WMImplant - https://github.com/FortyNorthSecurity/WMImplant
WMIOps (older) - https://github.com/FortyNorthSecurity/WMIOps
TOPIC OF THE DAY
WMI - Exploitation and Detection
Articles:
Will Schroeder - @ harmj0y
Article on settings needed to enable remote WMI
Matt Graeber BlackHat 2015 - Abusing Windows Management
Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor
Chris Truncer - WMImplant
Other WMI and Exploit Kits for Testing detection:
ASR rules for blocking wmi and psexec process creation
INTERVIEW:
What is WMI
Why do PenTesters and Red Teamers like it?
What are the components of WMI that IR and defenders need to know about
What should defenders, hunters, IR and Forensic people look for?
How to add WMI to your investigations
WMIC cmd line
CIMOM Registry key
HKLM\SOFTWARE\Microsoft\WBEM\CIMOM
Scan the WMI database
Can you block this type of attack, block the following from being accessible
Admin$
wmic /node:"<hostname or IP>" os get Caption
Change key
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\LocalAccountTokenFilterPolicy - set to “0”
Delete key
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\FilterAdministratorToken
Disable Remote RPC from the Firewall maybe
Disable DCOM
Testing lab configuration - See Will’s article below
Add the keys just mentioned
Check Windows firewall for Remote RPC
Test that you can get to Admin$
wmic /node:"<hostname or IP>" os get Caption
If it works, you will get the OS of the remote machine and be able to map the ADMIN$ share
What our testing showed
Impersonation level - “impersonation” + “identification”
9. How to test yourself
WIn Logging Cheat sheet
Humio
The tools discussed
-----------------------------------------------------------------------------------------------
BDIR Podcast Episode-004
TOPIC: Cloud based Log Management and/or On-Prem Log Management
OUR GUEST WILL BE:
Pieter Heyn - Sales Manager EMEA of HUMIO
Kresten Krab - CTO of HUMIO
SPONSORS OF OUR PODCAST
NEWS-WORTHY - FBI asks everyone to reboot their routers
Last week, security researchers at Cisco's cyberintelligence unit Talos warned of the attack: malicious software, dubbed VPNFilter, had infected an estimated 500,000 consumer routers in 54 countries and was targeting routers from Linksys, MikroTik, Netgear and TP-Link, and possibly others.
The FBI on Friday sent out a notice recommending that anyone with a small office or home office router reboot (turn on and off) their devices to stop the malware
https://www.scmagazine.com/fbi-seizes-domain-behind-vpnfilter-botnet/article/768558/
Reboot vs. Pull the Plug? BDIR says pull the plug !!!
MALWARE OF THE MONTH
Sadly, none of interest this month ;-(
SITE-WORTHY
1. BDIR - The whole list of Windows Logging Cheat Sheets
2. BDIR - Windows 10 and Windows Server 2016 Security Auditing and Monitoring Reference.docx
Guests - HUMIO
Humio of course - https://www.Humio.com
TOOL-WORTHY
BDIR - Audit your logs to see where your audit logging compares to industry standards - LOG-MD
2. BDIR - Add additional details to your logs - The Sysmon Service
Guests - Humio
Humio of course - https://www.Humio.com
TOPIC OF THE DAY
Cloud based Log Management and/or On-Prem Log Management
Articles:
BACKGROUND - MG and BB
So why do I think this topic is important to IT, InfoSec, IR, Network, and Forensic people?
Why security and log management are important aka SIEM
Story about SMB needing help on an malware infection, multiple locations
MG Top 10 list of tools - Log Management is crucial to Detection and Response
Intro by Michael and Brian on how they found Humio
Humio was responsive to our suggestions
Other vendors were not, just said yeah, we just wanted your business
Cloud log management vs. on-prem
MG - I have looked at 10 or more logging solutions and the lack of ease of use is a big one
A good log management solution has to have some basic features a lot of solutions lacked or were very buggy
Easy to use console
Built-in alerting, not as an option
Exclusion ability, not this or this or this
Save reports and queries
Dashboards for those that want them
INTERVIEW:
Background of Humio
Live data vs query
No indexes used
Free vs Pro vs. trial vs. On-Prem solutions
How much data can I send in the 30 day trail for the SMB type use case?
Do you see yourself as a SIEM vendor or wanting to move there?
Not yet moving there
SectionGuard - Additional Windows information mentioned by Kresten
WLS (Windows Logging Service) mentioned by Michael
https://www.kcp.com/Partnering/Licensing-Technologies/Pages/kcp-software.aspx
How does GDPR or any compliance regulation affect Cloud shared hosting ?
And really is this just solved by going with an On-Prem solution?
What basic changes did you have to make being a Euro company in this space?
There are a lot of Logging solutions, what gap were you intending to fill; what problem were you trying to solve?
New features in the last release you want to mention
What are the major differences or advantages that your customers like about Humio?
Something NEW - INTRODUCING:
The “Windows Humio Logging Cheat Sheet”
11 Windows Event Log items to start with
Sample queries
Our goal for the listeners
Try it on your home systems
Learn how to do basic logging
How to audit a Windows system
How to set the audit logging
Install the WinLogBeat agent
Start with the Winlogbeat config from Malware Archaeology
Use Humio
Populate it with the queries from the "Windows Humio Logging Cheat Sheet"
-----------------------------------------------------------------------------------------------
BDIR Podcast Episode-003
TOPIC: The Incident Response Process, - Program, Plan, Policy, Process, Playbooks, and roles
our guest will be:
Lesley Carhart - Principal Threat Hunter at Dragos Inc.
Twitter: @Hacks4Pancakes
Blog: www.tisiphone.net
News-Worthy - City of Atlanta ransomware FOLLOW-Up
Atlanta Working 'Around The Clock' To Fight Off Ransomware Attack
ATLANTA SPENT $2.6M TO RECOVER FROM A $52,000 RANSOMWARE SCARE
Atlanta government was compromised in April 2017 – well before last week’s ransomware attack
Compromised Connected Fish Tank - Comes from a global threat report (2017) from Darktrace - a summary of their case studies for the year
Malware of the Month
Sigma Ransomware - Notable artifact
No text in the body of the message, just an image of text
Breaks any scanning of text for passwords to use in the attached Office documents by sandbox evaluation solutions
Site-Worthy
1. BDIR - ISO 27035 - Information security incident management
2. BDIR - NIST 800-61
Guest - Lesley Carhart
Tool-Worthy
BDIR - Blue Team Handbook: Incident Response Edition: A : by Don Murdoch GSE
BDIR - Blue Team Field Manual (by Alan J White and Ben Clark
Guest - Lesley Carhart
1. Didier writes lots of handy tools useful for forensics and IR. I use his pdf tools
2. A fair bit for inspecting suspicious attachments; rtfdump and oledump seem to do the same for OLE and RTF files.
Other tools Lesley recommends you learn:
Books Lesley recommends everyone read for IR
Blue Team Field Manual (BTFM) - by Alan White (Author), Ben Clark (Author)
Windows Internals, Part 1: System architecture, processes, threads, memory management, and more (7th Edition) 7th Edition - by Pavel Yosifovich (Author), Mark E. Russinovich (Author), David A. Solomon (Author), Alex Ionescu (Author)
Windows Forensic Analysis DVD Toolkit, Second Edition 2nd Edition - by Harlan Carvey (Author)
Digital Forensics with Open Source Tools: Using Open Source Platform Tools for Performing Computer Forensics on Target Systems: Windows, Mac, Linux, Unix, etc 1st Edition, Kindle Edition - by Cory Altheide (Author), Harlan Carvey (Author)
The Art of Memory Forensics: Detecting Malware and Threats in Windows, Linux, and Mac Memory 1st Edition - by Michael Hale Ligh (Author), Andrew Case (Author), Jamie Levy (Author), AAron Walters (Author)
Practical Malware Analysis: A Hands-On Guide to Dissecting Malicious SoftwareFeb 1, 2012 - by Michael Sikorski and Andrew Honig
Topic of the Day
The Incident Response Process, - Program, Plan, Policy, Process, Playbooks, and roles
The Program
ISO 27035 - Information security incident management
NIST 80-61 - Computer Security Incident Handling Guide (August 2012)
Plan
Incident Response Plan (sample) SEI
Model
PICERL - SANS
Prep, Detect/Analysys, Contain/Eradicate/Recovery, Post Incident Activity - NIST
Playbooks: (or “What to do in the event of...”)
Ransomware
Malware infection
Website defacement
Unauthorized Domain Admin Access
Multiple Simultaneous Logins
Media call / report of an incident from external entity
DoS
8. Phishing
9. Credential Stealing phishing
10. Lost or stolen equipment
11. When to use Forensics
12. How to do forensics
IESO - Cyber Security Forum - Playbooks
CERT SOCIETE GENERALE - IRM (Incident Response Methodologies)
(From a list found on Peerlyst)
Phishing
Virus or Worm
Ensure that the host has an updated virus definition file
Traffic Flows
Denial of service (Network Crafted)
Denial of service (spam)
Host Compromise (Trojan)
Network Compromise (Cracking)
Host Compromise (physical Access)
Domain Hijacking
Dns Cache Poisoning
Suspicious User Activity
User Account Compromised
Unauthorized Access (Employee)
Corporate espionage
Internet Hoaxes
IP Telephony denial of service or Outage
Unauthorized remote access protocol
Suspicious website access
Unexpected administrative account / permissions added.
Roles:
What is each person responsible for?
All the people add up to and are a part of your CIRT (NOT CERT)
Incident Responder / IR Manager
Incident Handler
Project Manager
Communication lead
Documentation lead
Security Operations Analysts / Triage Analysts
Forensic Analysts:
Malware Reversers
Security Engineering
Threat Intelligence
Leadership
HR
PR / Corporate Communications
Legal Council
IT (Domain Admin, Help Desk, Server Admins, Client / Patch Admins)
Audit
GRC / Disaster Recovery / Risk Management
Developers / AppSec / Product Engineering
War Room
What is it and when to use it and why
Tabletop Exercises
What should you do here
IR Firm Retainer & Fees can be used for?
What can you use them for?
Breach Notification
Who is involved
What to prepare
Whom to involve
Training:
Carnegie Mellon - SEI - CSIH
https://www.sei.cmu.edu/education-outreach/credentials/credential.cfm?customel_datapageid_14047=14324
SANS
-----------------------------------------------------------------------------------------------
BDIR Podcast Episode-002
TOPIC: Windows Logging: Who, What, Where, When, Why
OUR GUEST WILL BE:
David Longenecker - InfoSec Practitioner
Twitter: @dnlongen
Blog: SecurityForRealPeople.com
GitHub - https://github.com/dnlongen
News-Worthy - City of Atlanta hit with ransomware, services taken offline
Atlanta Working 'Around The Clock' To Fight Off Ransomware Attack
“Mayor (Keisha Lance Bottoms) told reporters that cybersecurity is now a top priority for the city.”
“Wi-Fi at Hartsfield-Jackson Atlanta International Airport has been shut down as a precaution”
Six days after a ransomware cyberattack, Atlanta officials are filling out forms by hand
“SecureWorks and the city's incident response team are working with law enforcement, including the FBI, Homeland Security and the Secret Service, as well as independent forensics experts and educational partners like Georgia Tech, to determine exactly what happened.”
“I am looking forward to us really being a national model of how cities can shore themselves up and be stronger because of it.” mayor said regarding digital infrastructure
http://malwarejake.blogspot.com/2018/03/atlanta-government-was-compromised-in.html
Malware of the Month
Dridex - Artifacts
This came in an email with a URL that auto downloaded and installed the malware, but could be a drive-by as well.
Since Dridex uses actual signed Microsoft binaries located in a different directory (not System32), sideloading is easy, it just has to be named after one of the Dlls that the binary actual needs in the same folder that is usually, and should be located in System32
This method has been making the Con circuit talks as many tools miss or exclude known good Microsoft signed binaries as “Good”. A popular tool we all use, Microsoft’s Sysinternals ProcessExplorer has an option we all have used to hide the Microsoft signed files to make it easier to see an obvious bad processes. Dridex exploits this typical behavior by analysts to hide among the known good.
It is important to note that we designed LOG-MD to see these cases since WHERE the file is located can be a BIG clue, even if it is a real and signed MS binary
Morphs on reboot - The DLL changes its hash on each reboot and the .EXE changes as well and the DLL named changed to what will work for that .exe. So chasing hashes is a waste of time. What you have hash wise is not what the rest of us will have.
5. Uses a valid trusted MS signed binary to launch the Bad DLL, which is named for a correct DLL that is needed by the launcher (GamePanel.exe, UxTheme.dll, CameraSettingsUIHost.exe, DUI70.dll, etc.)
6. Autoruns are a .lnk file in the users Startup folder and a Scheduled Task pointing to another version
7. Files are found in:
%windir%\System32\5_Char_random_name
%AppData%\5_Char_random_name
8. Uses SVCHost.exe to phone home and communicate
9. Opens a hole for Explorer in the Windows Firewall
Site-Worthy
Guest - David Longenecker
https://attack.mitre.org/wiki/Main_Page - Adversarial Tactics, Techniques & Common Knowledge. A repository of things for which to ask yourself, "would I detect this? Would it set off any alarms?"
https://jpcertcc.github.io/ToolAnalysisResultSheet/ - dozens of tools and exploitation techniques, with detailed artifacts generated by those actions. Again, a great resource for asking "how would I detect this?"
Tool-Worthy
LOG-MD
Guest - David Longenecker
https://blog.didierstevens.com/my-software/ - Didier writes lots of handy tools useful for forensics and IR. I use his pdf tools (https://blog.didierstevens.com/programs/pdf-tools/) a fair bit for inspecting suspicious attachments; rtfdump and oledump seem to do the same for OLE and RTF files.
Topic of the Day
Windows Logging, Who, What, Where, When, Why
Why is logging important?
Incident took place...what happened? I don’t know!
Research / hunting.
Alerts
Windows Default logging
Some of the improvements since XP
Default is painfully bad, so at minimum set the following
4688
5156
PowerShell
CMD Line Logging
Make checks for
Where does one start to improve logging
Industry Standards
Cheat Sheet(s)
Gaps in the industry standards
Why are they inadequate
Log configurations/properties
Log Sizes
FIFO
Centralized / forwarded vs. Local logging
Why some things shouldn’t be forwarded
Log “nice-to-haves” locally (it won’t kill the box -Microsoft Article)
What tools can you use to collect local logs?
Wevtutil
PowerShell
LOG-MD
Filtering logs on the endpoint
3rd party logging utilities
Sysmon
WLS
10. Advanced Logging
NEW - The Windows Advanced Logging Cheat Sheet
11. Log Attacks
Clear the logs
Stop the logging service
Change size to 1k
-----------------------------------------------------------------------------------------------
BDIR Podcast Episode-001
TOPIC: CREDENTIAL STEALING EMAILS WHAT CAN YOU DO
OUR GUEST WILL BE:
Martin Brough - Manager of the Security Solutions Engineering team in the email phishing industry
Topic of the day will be:
"Credential Stealing emails what can YOU do"
Show Notes:
Introductions
Introduce our Guest
Martin Brough
Twitters - @HackerNinja
Blog - InfoSec512.com
News-worthy:
The Register: Perv raided college girls' online accounts for nude snaps – by cracking their security questions. Personal info obtained to pull off 1,400 password resets. Now he's behind bars.
Powell's interest in all this was obtaining private sexually explicit photos, which people apparently store in their email accounts without much thought about security. It's not immediately clear why the large number of such images on the internet did not suffice.
Jonathan C. Powell, who hacked into over 1,000 email accounts in search of sexually explicit images and videos of college-aged women, was jailed for six months for computer fraud, the US Department of Justice said on Thursday.
"During that time frame, those Reset Utility accesses resulted in approximately 18,600 attempted password changes in connection with approximately 2,054 unique [Pace] email accounts, and approximately 1,378 successful password changes in connection with approximately 1,035 unique [Pace] email accounts," explained FBI special agent Christopher Merriman in the complaint.
2. The Hacker News: Beware! Undetectable CrossRAT malware targets Windows, MacOS, and Linux systems
The article states that “As CrossRAT is written in Java, it requires Java to be installed" Not entirely true, as the dropper can check for java, if none is present, can download JRE and run locally or can install “jportable launcher”.
Also, it is interesting that the article calls it undetectable in the title, but then tells you how to detect it by looking for a runkey.
3. Windows 10 Creator update breaks purposefully set security tweaks
4. TrickBot
Artifacts
Delivered by a Word Doc with Macros
So cscript and PowerShell to grab the dropper
PS gets the dropper and also launches one of the batch files to load
Stores files in %appdata%, so Appdata Roaming\localservice
Some oddly named binary
Client_ID file
Group_tag file
A directory named Modules
You can see a couple batch files in %temp% and the binary before it is copied
Persistence is a Task called “services update”
Named Pipes connection for PowerShell
The IP it uses was a US based hosting service
Site-worthy:
BDIR Pick
MalPedia - reports and info on malware families and their actors and yara signatures
https://malpedia.caad.fkie.fraunhofer.de/families
Malware Arch - Malware Reports
Martin - https://cymon.io/
Martin - https://domainIQ.com
Tools-worthy:
BDIR Picks
Put full URL into it so it can read the bad page
Good Screen Shot
Use the "Tools" option to get more data about the site - get ASNs as well
WhoIs, ASNs, Created Date, Country, IP
Screen Shot
Country, IP, ASN
Short Blacklist list
I prefer this one because it is US-based.
https://fortiguard.com/webfilter
Generally has the most current blacklist status (their own)
Also gives country
Safety Reputation
Domain age
https://talosintelligence.com/
Reputation details, web category
Country with map
Martin’s Picks
LOG-MD - www.LOG-MD.com
Sherlock
Topic of the DAY
Credential Stealing emails what can YOU do….
What to look for if you DON’T have a lab or also in your lab
Screen Shots – Good indicator a credential stealing site with an authentication page
Domain age - How old is the website in days or years. Is it new? DGA (Domain Generating Algorithms)
Blacklists – Is the domain in any blacklists, if so, why is the SMTP gateway not catching it
Category – Has the site been categorized (BLOG/Malware/etc.)
Reputation – Is this a Bad, Neutral or Good site
Country – Where is this URL from
Alexa Rating - How known is it
Evaluating it in a Lab
LOG-MD Babbeeeee
Steps to take when you get a Phishing email
1. Of course.. You get an alert of some kind or are notified
2. Get a copy of the email - You can’t evaluate it if you don’t have an actual copy, your help desk copy might not have the context correct
3. Evaluate the URL
In a lab, click all the way through, login too (fake creds)
Or with one of the URL eval sites
4. Block the URL - Ya need a Web Proxy of course
Or the IP in the firewall
5. Monitor the IPs in log management from your firewall logs
Who else went there
You will have a HUGE gap for offsite/roaming people
6. Consider Fast and Mass disabling of accounts
7. Recall the message from your mail servers
Keep people from opening it
8. Monitor any Internet facing non-2-Factor email logins
Unless you reset all your users that received the phish
9. Monitor any Internet facing non-2-Factor VPN logins
Unless you reset all your users that received the phish
10. Monitor any Internet facing non-2-Factor Cloud Storage logins
11. Monitor any Internet facing non-2-Factor Virtual Desktop logins
12. Monitor for password resets to make sure you got everybody
13. Contact the sender to say you have been owned
Assuming you know it actually came from them.. SMTP logs
14. Create a Report
What happened, how did it come in
What improvements can be made to avoid it
Improvements to monitoring or hunting
15. Update your Email Investigation process
You will improve each time
Someone will need to do this when YOU are not at work or sleeping
BDIR Podcast Episode-000
TOPIC: WHAT IS THIS NEW PODCAST ALL ABOUT, WHAT WILL IT COVER?
OUR GUEST WILL BE:
Dave Cowan - Forensic Lunch Podcast and G-C Partners
Tyler Hudak - Trainer in Malware Analysis and Reverse Engineering
Brian and I will kick off this new podcast, and the topic of the day will be:
"What is this new podcast all about, what will it cover?
Incident Response, Malware Discovery, and Basic Malware Analysis, Detection and Response, Active Defense, Threat Hunting, and where does it fit within DFIR"
Show Notes:
Introductions
Introduce our Guests
Tyler Hudak
Dave Cowan
News-worthy:
401k fraud - loans taken out using breach data
NC School - Emotet - Emotet malware compromised Rockingham County Schools servers after employees opened phishing emails - isn’t this why are doing this Podcast? Because people need to know they can clean this stuff up
Rockingham County School Board Vice Chair Bob Wyatt confirmed the cost of $314,000 for the repairs. The money, he said, will come out of the unrestricted fund
2-month, $314,000 service contract
The contract will staff 10 Level 3 and 4 engineers a total of 1,200 total onsite man hours. The company will also provide virus mitigation services, including a plan of attack and onsite imaging for approximately 12 servers and 3,000 client systems
Approximately 20 physical and virtual servers will be need to be rebuilt by hand
The cleanup is expected to take less than 30 days
Despite the approval of the contract, some questions did arise from board members who were curious as to why the board did not offer to take outside bids for the $314,000 project
Emotet details and artifacts
Artifacts:
Delivered via an Office Document
Please disable your macros !!!! Allow by exception
Uses PowerShell to fetch payload - Word calls PS = BAD
Checks to see if it is being evaluated in a Sandbox
Directories created for checks
C:\a
C:\123
Creates a service for persistence
Some create a Scheduled Task too (Services Update)
Startup folder
Files dropped in
C:\Windows\
C:\windows\system32\
C:\Windows\Syswow64\
C:\Users\<user name>\AppData\Local\Temp\
C:\Users\<user name>\AppData\Local\Random\
C:\usersd\<user name>\AppData\Roaming\Microsoft\Windows
IP’s - detect from your firewall
Site-worthy:
BDIR Pick
Tyler’s Pick
Brad Duncan’s Malware Traffic Analysys
Dave’s Pick
Phill’s - This week in Forensics as well
Tools-worthy:
BDIR Pick - Shameful self promotion - LOG-MD…
Dave’s Picks - Tri-Force, of course.. It is his tool
File system events parser - MAC OS
Tyler’s Pickl - Lazy Office Analyzer
Topic of the DAY
What is this new podcast all about? Incident Response, Detection and Response, Active Defense, Threat Hunting, Malware Discovery, Basic Malware Analysis
Define IR
The process by which you respond to an incident (legal sense)?
Do we agree on the diagram above?
Define Discovery
Define Analysis
Define Forensics
Does IR include preparation for an attack?
What is Active Defense?
Your definition will vary
Threat Hunting - where do Hunters fit into all of this?
JP.Cert paper
BDIR Podcast Sponsor:
LOG-MD.Com
This Podcast Sponsored by:
secshoggoth.blogspot.com
Show Notes:
ANNOUNCING The Incident Response Podcast
Brian and I are embarking on an expansion of the The Incident Response Podcast.
This will be a once a month podcast with a few extra casts here and there. The focus will be in the area of Detection and Incident Response, Malware Discovery, Basic Malware Analysis, Threat Hunting and improvements to your overall security posture.
COMING JAN 2018
Join us !